Security Assessment
Identify risks. Prioritize actions. Strengthen posture.


Identify Risks, Strengthen Defenses, and Stay Audit-Ready
A strong security posture starts with knowing where you’re exposed. LA Technologies’ Security Assessment provides a comprehensive, evidence-based evaluation of your IT and OT environments—so you can make informed decisions, fix critical gaps, and enforce consistent security across all locations.
Why Security Assessment Matters
Unknown Vulnerabilities
Hidden misconfigurations, outdated devices, and weak policies create openings for attackers.
Compliance Pressure
Audits demand documented controls, evidence, and continuous improvement.
Multi-Location Complexities
Inconsistent controls across branches lead to uneven risk.
Operational Continuity
Prevent outages and security incidents that disrupt business and safety.
Assessment Scope
We tailor the assessment to your environment and priorities.
Network Security
- Firewall rules, segmentation, VPN configurations
- Routing/switching baselines, remote access policies
- IDS/IPS policies, logging and alerting coverage

Endpoint & Server Security
- Patch status, AV/EDR, hardening baselines
- Local admin usage, removable media, application control
- Backup integrity and restoration drill readiness

Identity & Access
- AD/Azure AD hygiene (users, groups, roles)
- MFA usage, privileged access controls
- Password policies and account lifecycle processes

Email & Web Security
- Anti-phishing, anti-malware
- SPF/DKIM/DMARC
- DLP policies, web filtering, safe browsing controls
OT / Industrial Security (if applicable)
- Network segmentation between IT/OT
- Remote vendor access governance and jump hosts
- Asset inventory, firmware status, protocol exposure
- Safety-critical change controls and maintenance procedures

Physical & Environmental
- Access controls, surveillance, secure racks and wiring
- Device labeling, asset custody, visitor/vendor processes

Policies & Governance
- Security policies, SOPs, incident response runbooks
- Roles & responsibilities, training & awareness
- Evidence collection and audit readiness
Our Methodology
Planning & Scoping
Planning & Scoping define sites, systems, and priorities; agree on timelines and stakeholders.
Data Collection
Workshops, configuration reviews, log analysis, and controlled testing.
Technical Testing
Vulnerability scanning, configuration benchmarking, and sample validation.
Gap Analysis
Map findings to standards and your business impact.
Risk Prioritization
Rate risks by likelihood, impact, and ease of remediation.
Recommendations & Roadmap
Practical fixes, quick wins, and phased improvements.
Validation & Sign‑off
Review actions taken, update evidence, and finalize reports.
Standards & Frameworks We Align To
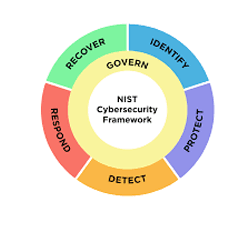
NIST Cybersecurity Framework (CSF)

ISO/IEC 27001 (controls and audit readiness)

IEC 62443 (for industrial/OT environments)

CERT-In advisories (India-specific guidance)

OEM Best Practices (firewalls, endpoints & network gear)
Deliverables You Receive
Executive Summary
Clear overview of risks and business impact, designed for leadership review.
Detailed Findings Report
Evidence, severity ratings, and affected assets for technical teams.
Prioritized Remediation Plan
Quick wins, medium-term actions, and strategic upgrades to improve posture.
Policy & Config Baselines
Templates for standardization across branches and new deployments.
SLA-Ready Action Tracker
Assign tasks, owners, and due dates—ready for immediate execution.
Review Workshop
Walkthrough with stakeholders to align next steps and clarify findings.
Multi-Location Coverage
Consistent Templates & Baselines
Applied across all branches uniformly.

Comparative Scorecards
Highlight site-wise risk differences effectively.


Phased Remediation Plan
Designed for efficient region-wise rollout

Centralized Evidence Repository
Evidence repository for audits and reviews.
Benefits with LA Technologies

Engagement Options
Rapid Security Health Check
1–2 Weeks
Quick baseline and top risks assessment for rapid insights.
Comprehensive Assessment
3–6 Weeks
Full-scope multi-location deep dive into all assets.
OT-Focused Assessment
Specialized
Tailored specifically for industrial and operational environments.
Ready to assess your security posture across locations?