Managed SIEM Platform
What is SIEM?
Security Information and Event Management (SIEM) is employed by businesses across a variety of industries to realize insight into activities in their IT estate, and to detect and answer potential threats. Originally, SIEM software was wont to collect, analyse and report on log data, however, the answer has evolved since into wider threat management. Modern SIEM solutions have additional capabilities and are ready to give businesses actionable insights into any threats or vulnerabilities within their infrastructure.
Once a particularly fashionable security approach, you’ll now hear rumours that SIEM is ‘dead’, or that it not has the required requirements a contemporary security system needs. However, this isn’t true. SIEM has evolved into a comprehensive, sophisticated solution, with advanced machine learning capabilities and threat management – making it the right solution for organisations wanting better, actionable insight into their security.
How does SIEM work?
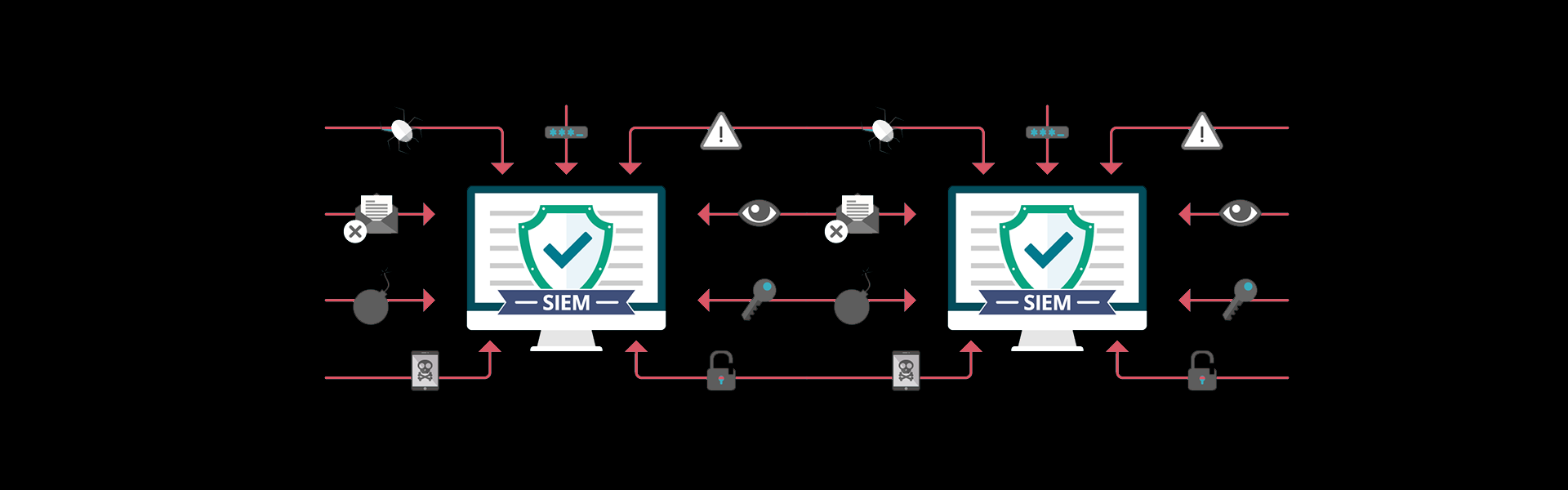
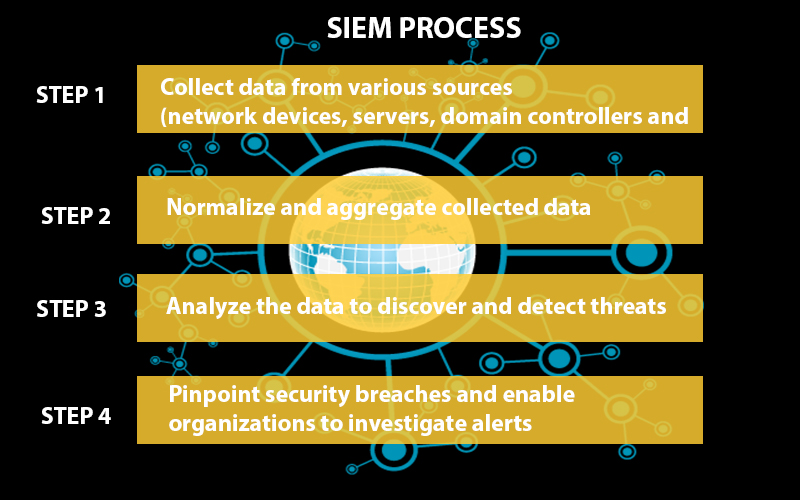
SIEM software collects log and event data across an IT infrastructure and collates it together in one central platform. It works by installing a search to a cloud service, which is then ready to identify all assets on your network, and see if there are any vulnerabilities, or threats. Then, it can sort these into categories like malware activity, failed logins, and other potential suspicious activity.
Essentially, a SIEM platform is in a position to sort huge amounts of knowledge into a funnel, which is then correlated using machine intelligence, so as to differentiate between suspicious and normal activity. If any activity is found to be suspicious, the SIEM platform identifies these incidents, and alerts users to deal with them. On the entire , it helps businesses better protect themselves from security breaches, and stay compliant.
SIEM Capabilities
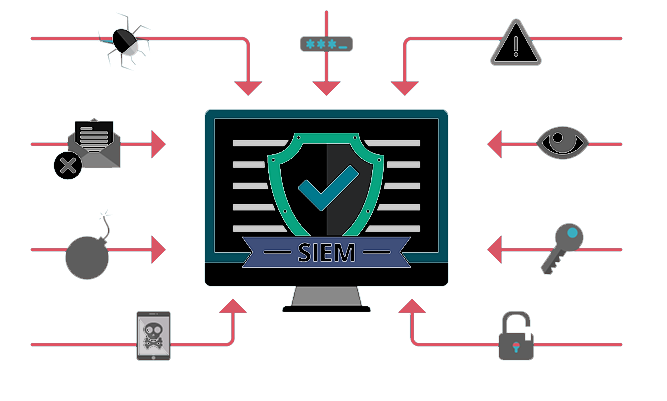
At its core, a SIEM platform’s main capabilities are to spot threats and vulnerabilities, provide reports on security-related incidents (such as unsuccessful logins) or malware activity, and send alerts supported whether or not these incidents are a possible security issue.
However, SIEM software has evolved in recent years, and may offer organisations far more in terms of capabilities and business benefits. With a contemporary SIEM solution, you’re able to:
Log management across your entire estate
Log management is probably the foremost well-known aspect of SIEM, and it involves collecting and storing log data from multiple disparate systems in one central location. latest SIEM solutions cover almost a whole IT estate, including public and personal cloud, data centres, actual network devices, servers and endpoints.
Security incident and event correlation
With so much activity happening simultaneously across your assets, it can be difficult to pinpoint what is and isn’t suspicious, which is why SIEM often allows you to set predefined rules; for example, how many login attempts can be done before the activity is flagged in the system as suspicious. This can be correlated across your IT estate, making it simpler to see the connection between your various systems.
Machine learning
One of the foremost useful capabilities of a SIEM solution is its ability to find out the way to find threats automatically, with none user input. This not only saves you time, but improves the efficiency of your overall threat management.
Dark web monitoring
Keeping your credentials safe may be a priority of the many businesses, which is why many modern SIEM solutions are ready to monitor the dark web, and make sure that none of your information is circulating, or in danger
Single dashboard view of all security issues
Arguably, how good your SIEM solution’s capabilities are means little or no if your security team is unable to know potential threat reports once they come through.
Therefore, many SIEM solutions present all of your data in an easy-to-digest, single format, in order that security professionals can get the knowledge they have relatively easily. Were it not for a centralised dashboard, your security team would need to find these threats manually – which can likely be both extremely difficult and time consuming.
Categorisation of all potential security threats
A SIEM solution will take all potential threats and categorise their severity, also as what quite issue it is; for instance , if it’s someone trying to take advantage of your credentials, an environmental problem (such as passwords stored in plain text) or if it’s an actual cyber-attack. Predetermined priority means the software can give each potential threat a risk score, so you’ll be alerted instantly to any security issues.
Ultimately, SIEM is extremely useful for contemporary businesses. Collecting and categorising information across a whole infrastructure, then reporting on suspicious activity manually would be virtually impossible. SIEM’s threat intelligence makes it much easier for organisations to realize better insight into their IT security and helps protect them from serious security threats.
What are the best SIEM tools?
There are variety of SIEM tools on the market available for a spread of business sizes and during a number of various formats, like cloud-based software, hardware or virtual appliances, and even more traditional server software. counting on your individual requirements, it’s worth researching which can be the simplest fit your business – however, as a start line it’s essential that your SIEM solution is in a position to:
- Improve the way you collect and manage your logs
- Help you better achieve your compliance targets
- Better manage security incidents and events
- Enhance the way you answer security breaches
Generally, SIEM tools are differentiated by cost, the features they need , and the way easy they’re to use – and buyers must weight up these against one another so as to make a decision which solution is best for them. Many tools, like Splunk and QRadar, are mainly enterprise-level solutions, and should not be suitable for smaller businesses with less budget. Additionally, some SIEM tools, like AlertLogic, aren’t sold as standalone product, and need to be purchased as a service – which, while understandable (as SIEM are often difficult to configure in house) isn’t necessarily the simplest option for a few businesses.
These are just a few of the considerations you would like to require when deciding which SIEM tool is that the best fit your organisation. because the preferred solution here at Ideal, AlienVault is a superb all-in-one solution that for us, may be a standout among its competitors. With all the capabilities you would like , you’re ready to monitor end points, user behaviour and network intrusion – with excellent overall asset management.
As the solution is entirely cloud-based, it are often scaled easily, and it possesses an enormous number of plugins and integrations with many other vendors traditionally seen throughout an IT network. It also can protect you right ‘out of the box’ – with a really easy setup process which will be done quickly, so you begin to ascertain value directly .
Whichever SIEM solution you opt is best for your business, you’ll got to consider whether you’ve got the required capability to manage a SIEM solution in house, or if leveraging a managed SIEM service would be a far better option.
About Us
The 18-year history of L A Technologies Pvt.Ltd is one that speaks of the evolution of a company by a visionary, Mr. Lawrence Albert, and of its employees, who have helped businesses and governments apply information technology to achieve new levels of competitiveness and success.
Branch
- Unit No. 1, 1st Floor, Besides Reliance Digital, Sion Trombay Road, Chembur (East). Mumbai. Pin code: 400 071.
- sales@la-technologiesindia.com
- +91 22 61828400
© Copyrights 2010. All rights reserved. by / L A Technologiesindia.com
